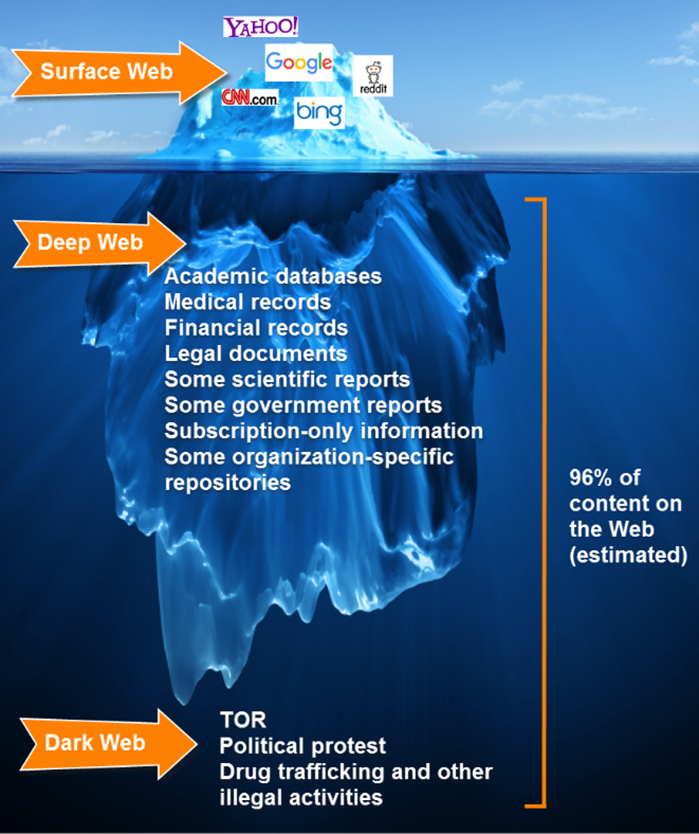
 We have all heard of the Dark Web, but do you know what it really is? When we hear the term, we think of hackers sitting in a dark room waiting or actively hacking into a government or corporate network. Those guys wouldn’t be after information on your computer, would they?
We have all heard of the Dark Web, but do you know what it really is? When we hear the term, we think of hackers sitting in a dark room waiting or actively hacking into a government or corporate network. Those guys wouldn’t be after information on your computer, would they?
The truth is that most cyber-criminals do not care who they hack. They have programs that gather information to be sold or used later. The programs are extremely easy to use and there is a market for them…on The Dark Web. But you work for or own a small company. Why on Earth would they want your information? Well, think about it. Does your company store social security numbers, employee names and addresses, how about the names of employees’ spouse or children? Birthdays, the street you grew up on, the first school you attended, your mother’s maiden name. All these things are confidential, at least in the sense that you wouldn’t want a total stranger to know them. They are often time ‘challenge questions’ used by your banking or credit card websites. In other words, it’s not just about nuclear launch codes and company patents anymore. In fact, just as an example, let’s suppose your company does payroll in-house. With just a couple of clicks, addresses and bank account information can be changed to send your payroll check almost anywhere in the world. What’s worse is that no one will likely catch it until it’s too late. Then either the employee or the company is out of that money.
What else do cyber-criminals do with the information they collect? If they aren’t using it themselves. they can put it for sale on The Dark Web. The Dark Web isn’t something that you can access from a Google search page or your favorite Windows browser address bar. There are special browsers that let you access this criminal network. Once on The Dark Web, information such as phone numbers, driver’s license numbers, credit cards, social security numbers, etc. can be previewed and bought. In fact, it’s a lot like eBay. All you have to do is click the information you want, add it to your cart, and pay for it (most payments are sent off-shore). It’s not just information that is sold though. There are also programs that can be purchased to help criminals and some would-be criminals steal information from unsuspecting targets. The programs sometimes even come with user manuals.
Other types of information that should be considered confidential:
Zip Codes – When using a gas pump, always cover the keypad when entering your zip code or your debit card PIN. Why? If someone clones your card and has the security information that is required by a retailer, then s/he can use it without your knowledge. Think of all the people you hand your credit and debit cards to throughout your day. Bartenders/waiters, cashiers, online ordering apps and sites are just a few examples.
Gas pump card readers are also a real danger (even in Middle TN). The United States Secret Service has stated that there have been service stations in Middle TN that were used to collect credit card information by using card skimmers. Card skimmers are devices that are placed over the top of the scanning device of gas pumps and other types of credit card readers. A few years ago, I attended a conference in which this type of theft was explained. By the time you realize that your information has been copied, it could be on The Dark Web just waiting for the highest bidder. What can you do? According the United States Secret Service, always check the card reader before you insert your card. Check to see if anything comes off the pump or card reader. If something comes off, NO NOT inform the retailer. After all, the retailer could be the criminal. Contact the FBI directly to report it. The Tennessee FBI telephone number (Memphis for Middle TN) is (901) 747-4300 or your can use your browser and go to tips.fbi.gov.
Social Media Posts – Most people do not realize it but your phone will record the GPS coordinates of your pictures; that is, unless you turn that feature off. The feature is on by default. Predators of all types, including sex offenders and child molesters, can use this information to track down a location of their prey. Also, be careful about posting vacation pictures while you are on vacation. When you post pictures of you and your family at the beach, criminals now know your house is not occupied. See why your home address is confidential?
Free games on your phone or computer – Most people, unless they’re learning to program or writing a game for a few friends, are not going to spend hours writing code, developing graphics, and marketing games so that they can make a free app. Think of all the games that are advertised free. Remember those pop-up ads? “They’re there for a reason. Someone or some company is paying to advertise within the ‘free game’. The more people that download and play the game the better. After-all, it’s advertising.
Advertising is probably the least concern when speaking about free games. Free games can come with malware and other cyber-spying software included. Each time you click, your phone can record your keystrokes, your fingerprints, and even determine your thinking patterns for playing the game. This isn’t something most of us would consider useful information we would want but, to cyber-criminals, it is a gold mine.


